A special gift on dewali by nabab on street ......great job
Thursday, October 27, 2011
Monday, October 17, 2011
Cross-site scripting (XSS)
Cross-site scripting (XSS) is a type of computer security vulnerability typically found in web applications that enables attackers to inject client-side script into web pages viewed by other users.
A cross-site scripting vulnerability may be used by attackers to bypass access controls such as the same origin policy. Cross-site scripting carried out on websites accounted for roughly 80% of all security vulnerabilities documented by Symantec as of 2007.Their effect may range from a petty nuisance to a significant security risk, depending on the sensitivity of the data handled by the vulnerable site and the nature of any security mitigation implemented by the site's owner.
Download
A cross-site scripting vulnerability may be used by attackers to bypass access controls such as the same origin policy. Cross-site scripting carried out on websites accounted for roughly 80% of all security vulnerabilities documented by Symantec as of 2007.Their effect may range from a petty nuisance to a significant security risk, depending on the sensitivity of the data handled by the vulnerable site and the nature of any security mitigation implemented by the site's owner.
Download
Saturday, October 1, 2011
How to change property of any software.
Here I have shown you property of VLC Media player.Copyright is not of vlc media player instead of that copyright is to "Hackingforever".you can change all the property not only of vlc media player but other software as well.just fallow these simple steps and take copyrights to you and impress the people.
Step1:Download resource hacker by typing it in google or from this link.
http://www.softpedia.com/progdownload/Resource-hacker-download-1520.html
step2:
open the exe file in resource hacker.
step3:
In left side you can see some option like icon
,icongroup,versioninfo and may be some other option depending on the software for which you are going to make some changes.
step4:
Click on version info then 1033.here in right side you can see properties of vlc just change it. click on compile script then save it on some place.
step5:
Rename it and give origanal name of software.copy it paste it on original location(where from you had opened the original soft).
step6:
Make a right click on soft go to details tab and you can see changes have made here.
note:
1)If you are opening any system file(windows file),then copy it first to another location then make changes and paste it on previos location.
2)you may required to mange permissions that I have already discussed in previous post.
3)open resource hacker as administrator.
Step1:Download resource hacker by typing it in google or from this link.
http://www.softpedia.com/progdownload/Resource-hacker-download-1520.html
step2:
open the exe file in resource hacker.
step3:
In left side you can see some option like icon
,icongroup,versioninfo and may be some other option depending on the software for which you are going to make some changes.
step4:
Click on version info then 1033.here in right side you can see properties of vlc just change it. click on compile script then save it on some place.
step5:
Rename it and give origanal name of software.copy it paste it on original location(where from you had opened the original soft).
step6:
Make a right click on soft go to details tab and you can see changes have made here.
note:
1)If you are opening any system file(windows file),then copy it first to another location then make changes and paste it on previos location.
2)you may required to mange permissions that I have already discussed in previous post.
3)open resource hacker as administrator.
Tuesday, September 27, 2011
What are the port exactly and how can use it for a HACKER's point of view.
hey guys how are you? write it .it is really important for me....
In this post I am going to tell you about Port.What the port is?
well, there are basically two kind of ports -Physical (hardware) and Virtual (software).You may be know ports as a slots behind computer where we plug mouse ,keyboard. these are the physical ports but as you guys are hacker so i m sure you people are interested in virtual ports means software ports.
" A port is a virtual or physical pipe through which information flows.A particular computer can have a large no of ports.each port has it's uniqe port number and max of the port are used for services.
some popular ports and services running are:
ping 7
time 13
telnet 23
SMTP 25
whois 43
HTTP 80
Finger 79
SSH 22 (this is same as secure shell login)
For more information about port number just go to your favourite search engine
type RFC and read it
NOTE:
1:RFC stands for Request for comment.it cover each aspect of networking and internet.
2:for more info regarding port (not about port scanning because i will tell you port scanning in other post) can ask me 0n facebook www.facebook.com/ashutiwari4 or can simply type in comment box...
In this post I am going to tell you about Port.What the port is?
well, there are basically two kind of ports -Physical (hardware) and Virtual (software).You may be know ports as a slots behind computer where we plug mouse ,keyboard. these are the physical ports but as you guys are hacker so i m sure you people are interested in virtual ports means software ports.
" A port is a virtual or physical pipe through which information flows.A particular computer can have a large no of ports.each port has it's uniqe port number and max of the port are used for services.
some popular ports and services running are:
ping 7
time 13
telnet 23
SMTP 25
whois 43
HTTP 80
Finger 79
SSH 22 (this is same as secure shell login)
For more information about port number just go to your favourite search engine
type RFC and read it
NOTE:
1:RFC stands for Request for comment.it cover each aspect of networking and internet.
2:for more info regarding port (not about port scanning because i will tell you port scanning in other post) can ask me 0n facebook www.facebook.com/ashutiwari4 or can simply type in comment box...
How to create a VBS Deathly combo virus.
hey bodies,whasss up?
I think we have grown enough to know about VBScript or .vbs file type.Till now, we have knowledge about batch programing or .bat file type and we also know How to make virus in batch programing language.we have created many virus.for those who don't have knowledge about batch programing here i am giving an example..
Just write this one line code in notepad and save it with name.bat,code is
start name.bat
here file name should be same as starting file.
now here we are going to make some .vbs file.Just fallow these steps.
1).Open NOTEPAD
2).wrire code
3).save it with .vbs extention
it is as simple and similar as .bat file creation.
here are some codes given :
1).To give massage:-
ashu=msgbox("virus alert!!!!",,"hacker")
2)To know is your lapi or system male or female:-
CreateObject("SAPI.SPvoice").speak "I Love You Ashu"
In such way you can create some deathly virus of your own.You may take
help of bat file to create a vbs Deathly combo virus....
Note :
1) VBS file type introduce by microsoft in windows 98 so it will not work version of windows before 98
2)It was hint for you people to make you start in vbs programing in other post I will give some other virus code.
write your comment for this post......and did '+1'?
I think we have grown enough to know about VBScript or .vbs file type.Till now, we have knowledge about batch programing or .bat file type and we also know How to make virus in batch programing language.we have created many virus.for those who don't have knowledge about batch programing here i am giving an example..
Just write this one line code in notepad and save it with name.bat,code is
start name.bat
here file name should be same as starting file.
now here we are going to make some .vbs file.Just fallow these steps.
1).Open NOTEPAD
2).wrire code
3).save it with .vbs extention
it is as simple and similar as .bat file creation.
here are some codes given :
1).To give massage:-
ashu=msgbox("virus alert!!!!",,"hacker")
2)To know is your lapi or system male or female:-
CreateObject("SAPI.SPvoice").speak "I Love You Ashu"
In such way you can create some deathly virus of your own.You may take
help of bat file to create a vbs Deathly combo virus....
Note :
1) VBS file type introduce by microsoft in windows 98 so it will not work version of windows before 98
2)It was hint for you people to make you start in vbs programing in other post I will give some other virus code.
write your comment for this post......and did '+1'?
how to make your own software package with the help of windows..
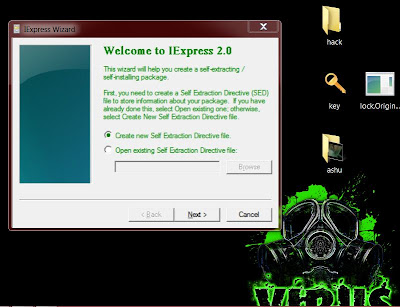
Hey guys want your own wizard (software may be a 'virus')in system32 .Don't be panic.Ashu is here just fallow these steps :
Step1:Write in run window 'iexpress'.this will open a window as you can see in image.
step2:
select one and click on next now you have 3 options select one of them click on next.Here now you can give any title to your package and click on next just do next.Again after reading instruction you can whether it will display licence or not.
step3:
Now you have to select the program may be your 'EXE' file produce by 'C'or '.VBS'or '.BAT' or'.ANY' as you wish...
step4:
After finishing this go to system32 and search the title.Here you can find your own software with your own certificate.....enjoy this.For example I have shown here a software which is made by me named 'Heart-locker' with my own certificate it shown here.
NOTE: here you can select the two or more file and you can bind it without any third party software. So,It can work like binder also with many high feature by microsoft it self.
Step1:Write in run window 'iexpress'.this will open a window as you can see in image.
step2:
select one and click on next now you have 3 options select one of them click on next.Here now you can give any title to your package and click on next just do next.Again after reading instruction you can whether it will display licence or not.
step3:
Now you have to select the program may be your 'EXE' file produce by 'C'or '.VBS'or '.BAT' or'.ANY' as you wish...
step4:
After finishing this go to system32 and search the title.Here you can find your own software with your own certificate.....enjoy this.For example I have shown here a software which is made by me named 'Heart-locker' with my own certificate it shown here.
NOTE: here you can select the two or more file and you can bind it without any third party software. So,It can work like binder also with many high feature by microsoft it self.
how to change maximum thing in windows look wise according to us or Be more familiar with registry.
Hey friends,Wass up??write it in comment box.....
In this post I am going to make you more familiar with the Registry Edit .here i am telling How can you change the color of links in my computer ,change the color password entries(by default it is black )or can change color of text in notepad or can change color of right click menu and for sure
lot more......So,what have you do? as previous fallow these number of steps.
1)Open regedit
2)go to HKEY_CURRENT_USER menu. and make a click.
3).click on CONTROL PANAL
4).Click to the COLORS
5).Here in right side you people can see lot of OPTIONS.So,make changs as you wish........is it simple or not???
NOTE:-
1)You people can make lot of changes from here .so, be careful because it may harm your computer,you can make backup before make changes....
2).Here you may have problum to change the color bacause it will be given like
0 0 0 or 255 255 255 or likewise something else..
" so what can you people do, just open ms paint go to the 'edit color'. here you can see there are three option of 'RED, GREEN, BLUE'. this is the sequence of colors put the value in box, get new color and make changes on registry."
3) Changes will apear after refresh so press 'F5', or after restart your computer.
just enjoy your changes.............
In this post I am going to make you more familiar with the Registry Edit .here i am telling How can you change the color of links in my computer ,change the color password entries(by default it is black )or can change color of text in notepad or can change color of right click menu and for sure
lot more......So,what have you do? as previous fallow these number of steps.
1)Open regedit
2)go to HKEY_CURRENT_USER menu. and make a click.
3).click on CONTROL PANAL
4).Click to the COLORS
5).Here in right side you people can see lot of OPTIONS.So,make changs as you wish........is it simple or not???
NOTE:-
1)You people can make lot of changes from here .so, be careful because it may harm your computer,you can make backup before make changes....
2).Here you may have problum to change the color bacause it will be given like
0 0 0 or 255 255 255 or likewise something else..
" so what can you people do, just open ms paint go to the 'edit color'. here you can see there are three option of 'RED, GREEN, BLUE'. this is the sequence of colors put the value in box, get new color and make changes on registry."
3) Changes will apear after refresh so press 'F5', or after restart your computer.
just enjoy your changes.............
Customize your Right Click
Customising the right click menu:
Hey guys, Now i m going to tell you how can you add a new option to your right click as shown in figure. just do it and enjoy.....
step1:
open regedit by typing it in run window.
step2:
Go to HKEY_CLASS_ROOT\Directory\Shell
Step3:
Right click on shell and create a new sub key by right clicking on the shell key and selecting new>key .type here, whatever msg you want on right click option(here i am assuming notepad and my 'msg is padai kar le @$|-||_|!!!').now click on msg 'padai kar le @$|-||_|!!!' and add a new key named command. here in right panal, modify the value with full path name of software, which is genrally-
c:\windows\system32\notepad.exe for notepad.
Step4:
Now press F5 and go on any folder make a right click on any folder and can find your option.
Note:
1:Here you can associate new software with some interesting name,for example you can write notepad, a newbie understand it will open notepad, insteed of this, it will open cmd window or any thing else as you wish.
2.you can make your right click more interesting by changing the msg.
enjoy it budies...
Hey guys, Now i m going to tell you how can you add a new option to your right click as shown in figure. just do it and enjoy.....
step1:
open regedit by typing it in run window.
step2:
Go to HKEY_CLASS_ROOT\Directory\Shell
Step3:
Right click on shell and create a new sub key by right clicking on the shell key and selecting new>key .type here, whatever msg you want on right click option(here i am assuming notepad and my 'msg is padai kar le @$|-||_|!!!').now click on msg 'padai kar le @$|-||_|!!!' and add a new key named command. here in right panal, modify the value with full path name of software, which is genrally-
c:\windows\system32\notepad.exe for notepad.
Step4:
Now press F5 and go on any folder make a right click on any folder and can find your option.
Note:
1:Here you can associate new software with some interesting name,for example you can write notepad, a newbie understand it will open notepad, insteed of this, it will open cmd window or any thing else as you wish.
2.you can make your right click more interesting by changing the msg.
enjoy it budies...
Adjust Your screen as you wish....
Guys this post will tell you how to make look of your computer large than now. So be ready fallow these steps and enjoy
step1:
Open regedit
Step2:
click on H_key_current_config
step3: now just click on software then fonts
step4:
here already there is given size nearly 60.Make it as you want
it may be lesser or larger.It's up to you ....
Note:
1:Who are using Terbo 'C' on Windows 7 it can be quite helpful for them
I am not saying you can use terbo 'C' in full screen but it will more reliable for sure.
step1:
Open regedit
Step2:
click on H_key_current_config
step3: now just click on software then fonts
step4:
here already there is given size nearly 60.Make it as you want
it may be lesser or larger.It's up to you ....
Note:
1:Who are using Terbo 'C' on Windows 7 it can be quite helpful for them
I am not saying you can use terbo 'C' in full screen but it will more reliable for sure.
Wednesday, September 21, 2011
how to hide drives using dos
Hello guys , we all wish to make our data more personal and secure from others .for this some times we have to make our partition hidden , for this purpose there are many softwares are in market but those are for computer illiterates . if you are a good with your computer skills then hiding partition drives are most simple thing to do in windows in very few time u can have mastery over it there are following steps given to hide your drives using dos . just follow the following steps and secure your data for free :
1. open the dos window or command prompt. goto run type cmd and then press enter.
2. type diskpart at command prompt. After this at dos u will get written diskpart>
3. type list volume to see your volume number.
note :on different computers the volume no. may be different so carefully watch the volume no.
4. now just select volume by using select volume command for e.g. select volume 2
5. now you have to only wright remove . and your drive gets hided.it might possible that your system requires restart after this, don't worry about that.
6. if you want to unhide your drive just follow above 4 steps as it is and after selecting volume type assign. and your drive gets unhided .
these are some simple and short steps to make your drive hiden .
Things to remember:
1. this methods only applicable to windows operating system.
2. you directly run the diskpart by typing it into run
1. open the dos window or command prompt. goto run type cmd and then press enter.
2. type diskpart at command prompt. After this at dos u will get written diskpart>
3. type list volume to see your volume number.
note :on different computers the volume no. may be different so carefully watch the volume no.
4. now just select volume by using select volume
5. now you have to only wright remove . and your drive gets hided.it might possible that your system requires restart after this, don't worry about that.
6. if you want to unhide your drive just follow above 4 steps as it is and after selecting volume type assign. and your drive gets unhided .
these are some simple and short steps to make your drive hiden .
Things to remember:
1. this methods only applicable to windows operating system.
2. you directly run the diskpart by typing it into run
manage permission for a file or folder in windows7 & vista
A lot of files and folders in Windows 7 & Vista does not actually belongs to users. Rather, most system files have “Trusted Installer” as owner, the assign or grant read+write, traverse or full control permissions to SYSTEM or CREATOR OWNER user account only. So users must take ownership and grant full access control permissions and rights to themselves if they want to modify, rename or delete these files or folders. Sometimes, users may need to take ownership and grant full rights to themselves on another drive or partition, especially on disk newly installed or inserted if they cannot browse the contents from the drive.
To take ownership and grant full control (or read write) permissions of files or folders in Windows Vista, do these steps.
1. In Windows Explorer window, locate the files or folders that you want to take ownership and grant or change full control or other access permissions.
2. Right click on the file or directory, and then select Properties on the right click menu.
3. Click on Security tab.
4. Click on Advanced button at the bottom.
5. In “Advanced Security Settings” dialog window, click on Owner tab.
6. Here you will be able to see current owner (i.e. TrustedInstaller). To take ownership of the object, click on the Edit button. If UAC prompts for administrator’s password or permission to continue, enter the correct password or press Continue button.
7. Additional “Advanced Security Settings” dialog will appear. Highlight the user name (for example, Administrators) in the Change owner to box that you want to assign as the owner for the object. Click OK to make the change.
8. Back in original parent level “Advanced Security Settings” window, you will see the existing owner of the file or folder has changed to the user you just selected.
9. Click OK button to exit this window.
10. Click OK again to exit completely from the Properties window.
11. The ownership is now belonged to user or user account that been selected. To assign necessary permissions to the user too, repeat step 1 to 3 to open the object’s Properties window again.
12. In object’s Properties window, click on Edit button to change permissions. If UAC prompts for administrator’s password or permission to continue, enter the correct password or press Continue button.
13. Highlight the Administrators or the user who wants the permissions on the object be changed in the “Group or user names” box.
If the user ID or group that you want to manage the permissions for the object doesn’t exist, click on Add button, and type in the user name or group name desired into the Enter object names to select box, and finish off by clicking on OK.
14. In the Permissions for Administrators box below (or any other user name or group name you chose), click on “Full Control” under the “Allow” column to assign full access rights control permissions to Administrators group.
15. Click “OK” twice when done.
Users can now do whatever you like to the files or directories processed as above. If you feel that above process is a little too long, and prefer to use command line to perform above process, then open an elevated command prompt as administrator, and issues the following commands:
For Files:
takeown /f file_name /d y
icacls file_name /grant administrators:F
For Folders or Directories (will perform action recursively):
takeown /f directory_name /r /d y
icacls directory_name /grant administrators:F /t
Replace file_name or directory_name with actual file name or folder name, with path when applicable. The first command will take ownership of the file or folder specified, and the second command will grant full control permissions to administrators user group. Note that when using command for folders, to command will run recursively. To prevent the task been perform recursively, remove the “/r” and “/t” switch.
Above two commands have been scripted in Windows command shell batch script that easily perform the task of taking ownership and grant full control permissions to Administrators user group by typing simple command. Alternatively, users can add “Take Control Of” option to right click menu so that the next time you need to take control of a file with full control permissions, it’s just a one click task.
Tuesday, September 13, 2011
Sunderdeep ke launde
Security_Accounts_Manager(SAM)
The Security Accounts Manager (SAM) is a registry file in Windows NT, Windows 2000, Windows XP, Windows Vista and Windows 7. It stores users' passwords in a hashed format (in LM hash and NTLM hash). Since a hash function is one-way, this provides some measure of security for the storage of the passwords.
In an attempt to improve the security of the SAM database against offline software cracking, Microsoft introduced the SYSKEY function in Windows NT 4.0. When SYSKEY is enabled, the on-disk copy of the SAM file is partially encrypted, so that the password hash values for all local accounts stored in the SAM are encrypted with a key (usually also referred to as the "SYSKEY").
In the case of online attacks, it is not possible to simply copy the SAM file to another location. The SAM file cannot be moved or copied while Windows is running, since the Windows kernel obtains and keeps an exclusive filesystem lock on the SAM file, and will not release that lock until the operating system has shut down or a blue screen exception has been thrown. However, the in-memory copy of the contents of the SAM can be dumped using various techniques, making the password hashes available for offline brute-force attack.
How to use themes in windows 7 home basic.
guys are u using windows 7 home basic and want to use themes.not worry do this and use themestep1:open regedit HKEY_CURRENT_USER/SOFTWARE/MICROSOFT/WINDOWS/DWM
STETP2:CREATE A NEW DWORD(32-BIT) RENAME IT AS UseMachinecheck with value 0
again make a new keyword(32-bit) with the name Blur with value 0
again do this with the name Animations with value 0
step4:open cmd prompt with admin
step5:type commands-
"Net stop uxsms" press enter
"net start uxsms"
step6:restart your computer and enjoy
STETP2:CREATE A NEW DWORD(32-BIT) RENAME IT AS UseMachinecheck with value 0
again make a new keyword(32-bit) with the name Blur with value 0
again do this with the name Animations with value 0
step4:open cmd prompt with admin
step5:type commands-
"Net stop uxsms" press enter
"net start uxsms"
step6:restart your computer and enjoy
how to give a massage before logon screen
Hey guys, here I am tailing you how to give a massage before log on screen. it is very simple just fallow these steps -
step1:open regedit by typing it in run(ctrl+r)
step2:goto the Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\currentVersion \polcies\system
step3:here in right side u can see there is option of ligalnotice .click on that and type your massages...as shown in fig.
step4: restart your computer
NOTE:there is two option of ligalnotice first one is heading and other one is massage.
step1:open regedit by typing it in run(ctrl+r)
step2:goto the Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\currentVersion \polcies\system
step3:here in right side u can see there is option of ligalnotice .click on that and type your massages...as shown in fig.
step4: restart your computer
NOTE:there is two option of ligalnotice first one is heading and other one is massage.
Monday, September 12, 2011
what is TCP ?
The Transmission Control Protocol (TCP) is one of the core protocols of the Internet Protocol Suite. TCP is one of the two original components of the suite, complementing the Internet Protocol (IP), and therefore the entire suite is commonly
referred to as TCP/IP. TCP provides reliable, ordered delivery of a stream of bytes from a program on one computer to another program on another computer. TCP is the protocol that major Internet applications such as the World Wide Web, email, remote administration and file transfer rely on. Other applications, which do not require reliable data stream service, may use the User Datagram Protocol (UDP), which provides a datagram service that emphasizes reduced latency over reliability.
referred to as TCP/IP. TCP provides reliable, ordered delivery of a stream of bytes from a program on one computer to another program on another computer. TCP is the protocol that major Internet applications such as the World Wide Web, email, remote administration and file transfer rely on. Other applications, which do not require reliable data stream service, may use the User Datagram Protocol (UDP), which provides a datagram service that emphasizes reduced latency over reliability.
Change your logon screen without any third party software.
hey if u guys wanna change your logon screen of windows. then fallow the steps
step1: Open computer\windows\system32\oobe
here oobe is folder where u have to go
step2: here in different version of operating system,
for windows7 goto info here is a image just change the permissions and replace file with image(u want on logon screen)
step3:goto the logon screen or restart computer..
your logon screen has been changed
Note :
1)for changing permissions see next Post
2)it may be u cannot find image in info folder but don't worry image is in oobe you have to search that and replace image.
3)name should be same (you have to change name of new image)with the old image(default logon screen)..
4)if u are getting some problem there is a page on facebook named hackingforever u can ask me over there or type in comment over here.
step1: Open computer\windows\system32\oobe
here oobe is folder where u have to go
step2: here in different version of operating system,
for windows7 goto info here is a image just change the permissions and replace file with image(u want on logon screen)
step3:goto the logon screen or restart computer..
your logon screen has been changed
Note :
1)for changing permissions see next Post
2)it may be u cannot find image in info folder but don't worry image is in oobe you have to search that and replace image.
3)name should be same (you have to change name of new image)with the old image(default logon screen)..
4)if u are getting some problem there is a page on facebook named hackingforever u can ask me over there or type in comment over here.
how to change default color of cmd fonts
Guys u have seen some time, whenever some start cmd prompt, By default the color of the font is not white or background is not black,but some thing else..
not worry i m going to tell u how to do this.....
step1:click on start
type regedit (stand for registry edit)
step2:click on HKEY_CURRENT_USER
click on Console
here u can see some option
just click on the screen color
put value data 2(u have option (0 to E)for different color )
press O.K
step3:open cmd and enjoy...
Note:from this option console u can make some other changes also....
but it can dump your computer also so be care ful...
not worry i m going to tell u how to do this.....
step1:click on start
type regedit (stand for registry edit)
step2:click on HKEY_CURRENT_USER
click on Console
here u can see some option
just click on the screen color
put value data 2(u have option (0 to E)for different color )
press O.K
step3:open cmd and enjoy...
Note:from this option console u can make some other changes also....
but it can dump your computer also so be care ful...
Friday, August 26, 2011
how to hide drives using dos
Hello guys , we all wish to make our data more personal and secure from others .for this some times we have to make our partition hidden , for this purpose there are many softwares are in market but those are for computer illiterates . if you are a good with your computer skills then hiding partition drives are most simple thing to do in windows in very few time u can have mastery over it there are following steps given to hide your drives using dos . just follow the following steps and secure your data for free :
1. open the dos window or command prompt. goto run type cmd and then press enter.
2. type diskpart at command prompt. After this at dos u will get written diskpart>
3. type list volume to see your volume number.
note :on different computers the volume no. may be different so carefully watch the volume no.
4. now just select volume by using select volume command for e.g. select volume 2
5. now you have to only wright remove . and your drive gets hided.it might possible that your system requires restart after this, don't worry about that.
6. if you want to unhide your drive just follow above 4 steps as it is and after selecting volume type assign. and your drive gets unhided .
these are some simple and short steps to make your drive hiden .
Things to remember:
1. this methods only applicable to windows operating system.
2. you directly run the diskpart by typing it into run
1. open the dos window or command prompt. goto run type cmd and then press enter.
2. type diskpart at command prompt. After this at dos u will get written diskpart>
3. type list volume to see your volume number.
note :on different computers the volume no. may be different so carefully watch the volume no.
4. now just select volume by using select volume
5. now you have to only wright remove . and your drive gets hided.it might possible that your system requires restart after this, don't worry about that.
6. if you want to unhide your drive just follow above 4 steps as it is and after selecting volume type assign. and your drive gets unhided .
these are some simple and short steps to make your drive hiden
Things to remember:
1. this methods only applicable to windows operating system.
2. you directly run the diskpart by typing it into run
how to hack a remote computer through telnet
Hack a remote computer with telnet Method 1:
Before looking at this method to Hack with telnet you must know that what are ports?There are two kinds of ports-Physical(HardWare) and Virtual(Software)You may be thinking of ports to be the slots behind your CPU to whichy ou connect your Mouse or Keyboard or your monitor. These sockets are called physical ports .We are here interested in only virtual ports.It is nothing physical but it is kind of a virtual pipe through which information can go in and out of the computer.
A particular computer can have a large number of ports. All ports are numbered .Now at each port a particular service is running. A software which runs on a port is called service . For interchanging different kinds of information different ports are used. A typical list shows the various ports
Ping : 7
Systat : 11
Time : 13
NetStat : 15
SSH : 22
Telnet : 23
SMTP : 25
Whois : 43
Finger : 79
HTTP : 80
POP : 110
Method 2
You can connect to a remote computer at a particular port. When you are connected to that port then you can interchange information related to that particular port only. Ports can be open or closed. If a particular port of a computer is closed then you can not connect to that computer
on that port. Generally most of the computers have atleast 5 or 6 ports open
First goto run and type telnet:
Once the Telnet windows pops up click on Connect->RemoteSystem then in the host name type the host i.e. the IP address of the remote computer or the website you want to connect to . Then in the Port select the port you want to connect to . You can only connect to ports which are open on the host computer.Almost always leave the TermType to vt100.We use vt100 as it is compatible with most monitors .
Then click connect and you will be connected to the remote machine in some time. The syntax of the telnet command from DOS prompt is C:\>telnet.
By default port is taken as 23. Scroll down and read more about ports
The first thing you have to do if you want to hack with Telnet, is find your local Telnet phone number.This can be done many ways. One way that always works, is to call up your local computer store, tel them that you recently purchased The Source or something like that, but that you lost the sheet that has the phone no. written on it.They'll tell it to you. (People who work in computer stores usualy aren't very smart
about that sort of thing.)
Call the number with your computer. Once the connection is established,
press twice. the computer will display "TERMINAL=" Type again. The computer will then display an at sign: "" Type in the access code here.:below are some access codes listed
(But please don't misuse it)
------------------------------------------------------------------------
Telemail
--------
To use the Telemail feature of Telenet, type mail at the "" prompt.
User id's are usually the first initial of the user's first name, plus
the last name.
eg- William gates= Wgates
-------------------------------------------------------------------------
C 20120 - VM 370 ONLINE
C 20124N- NEW YORK TIME INFORMATION SERVICE
C 20125 - NJIT ELECTRONIC INFORMATION
C 20130
C 20133
C 20138
C 20148
C 20154
C 20165
C 20166
C 20167 - WARNER COMPUTER SYSTEMS
C 20168 - WARNER COMPUTER SYSTEMS
C 20171
C 20182 - BANKERS TRUST CUSTOMER SERVICE
C 20184
C 20222
C 20225 - COMSHARE "COMMANDER II"
C 20246
C 20247 - GSD TIMESHARING
C 20270 - GSD TIMESHARING
C 202124- GENERAL MOTORS WARREN
C 202133
C 202138- (TYPE .HELP *)
C 202139- (TYPE .HELP *)
C 202140- (TYPE .HELP *)
C 202143
C 202144- (TYPE .HELP *)
C 202148
C 202149
C 202175 - HONEYWELL
C 202222 - GM PARTS
C 202229 - PRIMENET
C 20321 - WYLBUR
C 21221 - PRIMENET
C 21224 - PRIMENET
C 21225 - INTERACTIVE MARKET SYSTEMS
C 21226 - INTERACTIVE MARKET SYSTEMS
C 21228 - BURROUGHS NYC DATA CENTER
C 21229 - LANDART SYSTEMS
C 21231 - E.F.HUTTON
C 21233 - UNIVAC 1100
C 21247
C 21248
C 21252
C 21253 - VM/370 ONLINE
C 21256 - CITIBANK CASH MANAGER
C 21264 - CITICASH MANAGER INTERNATIONAL
C 21265 - CITICASH MANAGER INTERNATIONAL
C 21269
C 21281 - BANKERS TRUST CUSTOMER SERVICE
C 21284 - DATAMOR TIME SHARING
C 21288 - S-K WDC SYSTEM 1/ONLINE
C 212136 - (TYPE NEW/TSC)
C 212141
C 212142
C 212151 - CITICASH MANAGER INTERNATIONAL
C 212152
C 21255 - PRIMENET
C 21256 - PRIMENET
C 212160 - TELSTAT SIGMA 6
C 212167 - RSTS V.7.0-07
C 212168 - RSTS V.7.0-07
C 212171
C 212172
C 21284 - DATAMOR TIME SHARING
C 21325 - PRIMENET
C 21335 - MARKETRON RESEARCH AND SALES
C 21336 - MARKETRON RESEARCH AND SALES
C 21341
C 21360
C 21365
C 21366
C 213170 - DIALOG
C 21370 - XCC-WEST SYSTEM X2
C 21371 - XCC-WEST SYSTEM X3
C 21372 - XCC-WEST SYSTEM X3
C 21373 - XCC-WEST SYSTEM X1
C 21375 - XCC-WEST SYSTEM X2
C 21379 - INTERACTIVE SYSTEM/ONE
C 21384
C 21385
C 21386 - IAS PROGRAM DEVELOPMENT SYSTEM
C 21388
C 213105
C 21520 - TPF&C ONLINE
C 21534 - PRIMENET
C 21538
C 21722
C 21725
C 21726 - U OF I COMPUTING SERVICES
C 30121 - NASA RECON
C 30124 - SOURCE SYSTEM 10
C 30126 - DISTRIBUTIVE NETWORK
C 30128 - SOURCE SYSTEM 13
C 30134 - INTERACTIVE(GAITHERSBURG)
C 30135
C 30136
C 30138 - SOURCE SYSTEM 11
C 30147 - SOURCE SYSTEM 12
C 30148 - SOURCE SYSTEM 15
C 30149 - SOURCE SYSTEM 14
C 30320 - COMPUTER SHARING SERVICES
C 30330 - COMPUTER SHARING SERVICES
C 30335
C 30337 - PRIMENET
C 30339 - PRIMENET
C 30340 - PRIMENET
C 303125
C 30520
C 30522
C 30531
C 30532 - C.S.I. TIMESHARING SERVICE
C 30523 - C.S.I. TIMESHARING SERVICE
C 31231 - C.I.C. TIMESHARING
C 31232
C 31235
C 31236
C 31240
C 31247
C 31248
C 31249
C 31250
C 31254
C 31279
C 31289
C 312124
C 312127
C 31325
C 31327
C 31340 - ADP NETWORK
C 31341 - ADP NETWORK
C 31345 - PRIMENET
C 31359 - GENERAL MOTORS WARREN
C 31360 - GENERAL MOTORS WARREN
C 31361 - GM PARTS
C 31363 - VM/370 ONLINE
C 31370 - GM DECSYSTEM-20 TIMESHARING
C 31422
C 31423
C 31424 - MCAUTO VM/370 ONLINE
C 31425 - MCAUTO VM/370 ONLINE
C 31426
C 31432
C 31435 - PRIMENET
C 31444
C 31726 - RSTS V06C-04
C 40420
C 40434
C 40822
C 41520 - DIALOG
C 41527 - STANFORD IBM-3033A
C 41548 - DIALOG
C 41556
C 41560
C 41561
C 41562
C 41567
C 41580 - HARPER GROUP INFORMATION NETWORK
C 41587 - BUSSIPLEXER
C 51632
C 51633
C 51634
C 51638
C 51646
C 51647 - VM/370 ONLINE
C 51729
C 60320 - DARTMOUTH COLLEGE COMPUTING
C 60322
C 60324
C 60328
C 60331
C 60720
C 60942
C 60945
C 61114
C 61115
C 61118
C 61120
C 61221
C 61724
C 61735 - (TYPE D FOR SYSTEM) APPLIED LOGIC NETWORK CONTROL
C 61748 - PRIMENET
C 61750 - PRIMENET
C 61760 - (TYPE D FOR SYSTEM) APPLIED LOGIC NETWORK CONTROL
C 61766 - PRIMENET
C 61767 - PRIMENET
C 61770 - NDC-SYSTEM#
C 61774
C 61776 - NDC-SYSTEM#
C 61777 - NDC-SYSTEM#
C 61778 - PRIMENET
C 617120
C 617121
C 617124
C 617125
C 617127
C 617133
C 617135 - VM/370 ONLINE
C 61737 - VM/370 ONLINE
C 617138 - MASSACHUSETTS INSTITUE OF
C 617139 - MASSACHUSETTS INSTITUE OF
C 617140 - VM/370 ONLINE
C 617151
C 617152
C 617159
C 61763
C 61769 - (TYPE D FOR SYSTEM) APPLIED LOGIC NETWORK
C 61770 - BPL-INFORONICS
C 617171 - INTERACT LINE
C 617177 - ERT ENVIRONET
C 617178
C 617179 - ERT ENVIRONET
C 61780 - (TYPE HELP)
C 71424 - GLOBAL DATA TIMESHARING
C 71431 - (TYPE HELP)
C 71620 - UNION CARBIDE
C 80331
C 80423 - CONTROL DATA INTERCOM
C 80424 - CONTROL DATA INTERCOM
C 80426 - BABCOCK AND WILCOX
C 81623
C 81625 - UNINET
C 81626 - UNINET
C 90995D - TELENET NEWS SERVICE
C 91930
C 91931
C 91933 C 91934
Hope you liked the post,Pass the comments............
Before looking at this method to Hack with telnet you must know that what are ports?There are two kinds of ports-Physical(HardWare) and Virtual(Software)You may be thinking of ports to be the slots behind your CPU to whichy ou connect your Mouse or Keyboard or your monitor. These sockets are called physical ports .We are here interested in only virtual ports.It is nothing physical but it is kind of a virtual pipe through which information can go in and out of the computer.
A particular computer can have a large number of ports. All ports are numbered .Now at each port a particular service is running. A software which runs on a port is called service . For interchanging different kinds of information different ports are used. A typical list shows the various ports
Ping : 7
Systat : 11
Time : 13
NetStat : 15
SSH : 22
Telnet : 23
SMTP : 25
Whois : 43
Finger : 79
HTTP : 80
POP : 110
Method 2
You can connect to a remote computer at a particular port. When you are connected to that port then you can interchange information related to that particular port only. Ports can be open or closed. If a particular port of a computer is closed then you can not connect to that computer
on that port. Generally most of the computers have atleast 5 or 6 ports open
First goto run and type telnet:
Once the Telnet windows pops up click on Connect->RemoteSystem then in the host name type the host i.e. the IP address of the remote computer or the website you want to connect to . Then in the Port select the port you want to connect to . You can only connect to ports which are open on the host computer.Almost always leave the TermType to vt100.We use vt100 as it is compatible with most monitors .
Then click connect and you will be connected to the remote machine in some time. The syntax of the telnet command from DOS prompt is C:\>telnet.
By default port is taken as 23. Scroll down and read more about ports
The first thing you have to do if you want to hack with Telnet, is find your local Telnet phone number.This can be done many ways. One way that always works, is to call up your local computer store, tel them that you recently purchased The Source or something like that, but that you lost the sheet that has the phone no. written on it.They'll tell it to you. (People who work in computer stores usualy aren't very smart
about that sort of thing.)
Call the number with your computer. Once the connection is established,
press twice. the computer will display "TERMINAL=" Type again. The computer will then display an at sign: "" Type in the access code here.:below are some access codes listed
(But please don't misuse it)
------------------------------------------------------------------------
Telemail
--------
To use the Telemail feature of Telenet, type mail at the "" prompt.
User id's are usually the first initial of the user's first name, plus
the last name.
eg- William gates= Wgates
-------------------------------------------------------------------------
C 20120 - VM 370 ONLINE
C 20124N- NEW YORK TIME INFORMATION SERVICE
C 20125 - NJIT ELECTRONIC INFORMATION
C 20130
C 20133
C 20138
C 20148
C 20154
C 20165
C 20166
C 20167 - WARNER COMPUTER SYSTEMS
C 20168 - WARNER COMPUTER SYSTEMS
C 20171
C 20182 - BANKERS TRUST CUSTOMER SERVICE
C 20184
C 20222
C 20225 - COMSHARE "COMMANDER II"
C 20246
C 20247 - GSD TIMESHARING
C 20270 - GSD TIMESHARING
C 202124- GENERAL MOTORS WARREN
C 202133
C 202138- (TYPE .HELP *)
C 202139- (TYPE .HELP *)
C 202140- (TYPE .HELP *)
C 202143
C 202144- (TYPE .HELP *)
C 202148
C 202149
C 202175 - HONEYWELL
C 202222 - GM PARTS
C 202229 - PRIMENET
C 20321 - WYLBUR
C 21221 - PRIMENET
C 21224 - PRIMENET
C 21225 - INTERACTIVE MARKET SYSTEMS
C 21226 - INTERACTIVE MARKET SYSTEMS
C 21228 - BURROUGHS NYC DATA CENTER
C 21229 - LANDART SYSTEMS
C 21231 - E.F.HUTTON
C 21233 - UNIVAC 1100
C 21247
C 21248
C 21252
C 21253 - VM/370 ONLINE
C 21256 - CITIBANK CASH MANAGER
C 21264 - CITICASH MANAGER INTERNATIONAL
C 21265 - CITICASH MANAGER INTERNATIONAL
C 21269
C 21281 - BANKERS TRUST CUSTOMER SERVICE
C 21284 - DATAMOR TIME SHARING
C 21288 - S-K WDC SYSTEM 1/ONLINE
C 212136 - (TYPE NEW/TSC)
C 212141
C 212142
C 212151 - CITICASH MANAGER INTERNATIONAL
C 212152
C 21255 - PRIMENET
C 21256 - PRIMENET
C 212160 - TELSTAT SIGMA 6
C 212167 - RSTS V.7.0-07
C 212168 - RSTS V.7.0-07
C 212171
C 212172
C 21284 - DATAMOR TIME SHARING
C 21325 - PRIMENET
C 21335 - MARKETRON RESEARCH AND SALES
C 21336 - MARKETRON RESEARCH AND SALES
C 21341
C 21360
C 21365
C 21366
C 213170 - DIALOG
C 21370 - XCC-WEST SYSTEM X2
C 21371 - XCC-WEST SYSTEM X3
C 21372 - XCC-WEST SYSTEM X3
C 21373 - XCC-WEST SYSTEM X1
C 21375 - XCC-WEST SYSTEM X2
C 21379 - INTERACTIVE SYSTEM/ONE
C 21384
C 21385
C 21386 - IAS PROGRAM DEVELOPMENT SYSTEM
C 21388
C 213105
C 21520 - TPF&C ONLINE
C 21534 - PRIMENET
C 21538
C 21722
C 21725
C 21726 - U OF I COMPUTING SERVICES
C 30121 - NASA RECON
C 30124 - SOURCE SYSTEM 10
C 30126 - DISTRIBUTIVE NETWORK
C 30128 - SOURCE SYSTEM 13
C 30134 - INTERACTIVE(GAITHERSBURG)
C 30135
C 30136
C 30138 - SOURCE SYSTEM 11
C 30147 - SOURCE SYSTEM 12
C 30148 - SOURCE SYSTEM 15
C 30149 - SOURCE SYSTEM 14
C 30320 - COMPUTER SHARING SERVICES
C 30330 - COMPUTER SHARING SERVICES
C 30335
C 30337 - PRIMENET
C 30339 - PRIMENET
C 30340 - PRIMENET
C 303125
C 30520
C 30522
C 30531
C 30532 - C.S.I. TIMESHARING SERVICE
C 30523 - C.S.I. TIMESHARING SERVICE
C 31231 - C.I.C. TIMESHARING
C 31232
C 31235
C 31236
C 31240
C 31247
C 31248
C 31249
C 31250
C 31254
C 31279
C 31289
C 312124
C 312127
C 31325
C 31327
C 31340 - ADP NETWORK
C 31341 - ADP NETWORK
C 31345 - PRIMENET
C 31359 - GENERAL MOTORS WARREN
C 31360 - GENERAL MOTORS WARREN
C 31361 - GM PARTS
C 31363 - VM/370 ONLINE
C 31370 - GM DECSYSTEM-20 TIMESHARING
C 31422
C 31423
C 31424 - MCAUTO VM/370 ONLINE
C 31425 - MCAUTO VM/370 ONLINE
C 31426
C 31432
C 31435 - PRIMENET
C 31444
C 31726 - RSTS V06C-04
C 40420
C 40434
C 40822
C 41520 - DIALOG
C 41527 - STANFORD IBM-3033A
C 41548 - DIALOG
C 41556
C 41560
C 41561
C 41562
C 41567
C 41580 - HARPER GROUP INFORMATION NETWORK
C 41587 - BUSSIPLEXER
C 51632
C 51633
C 51634
C 51638
C 51646
C 51647 - VM/370 ONLINE
C 51729
C 60320 - DARTMOUTH COLLEGE COMPUTING
C 60322
C 60324
C 60328
C 60331
C 60720
C 60942
C 60945
C 61114
C 61115
C 61118
C 61120
C 61221
C 61724
C 61735 - (TYPE D FOR SYSTEM) APPLIED LOGIC NETWORK CONTROL
C 61748 - PRIMENET
C 61750 - PRIMENET
C 61760 - (TYPE D FOR SYSTEM) APPLIED LOGIC NETWORK CONTROL
C 61766 - PRIMENET
C 61767 - PRIMENET
C 61770 - NDC-SYSTEM#
C 61774
C 61776 - NDC-SYSTEM#
C 61777 - NDC-SYSTEM#
C 61778 - PRIMENET
C 617120
C 617121
C 617124
C 617125
C 617127
C 617133
C 617135 - VM/370 ONLINE
C 61737 - VM/370 ONLINE
C 617138 - MASSACHUSETTS INSTITUE OF
C 617139 - MASSACHUSETTS INSTITUE OF
C 617140 - VM/370 ONLINE
C 617151
C 617152
C 617159
C 61763
C 61769 - (TYPE D FOR SYSTEM) APPLIED LOGIC NETWORK
C 61770 - BPL-INFORONICS
C 617171 - INTERACT LINE
C 617177 - ERT ENVIRONET
C 617178
C 617179 - ERT ENVIRONET
C 61780 - (TYPE HELP)
C 71424 - GLOBAL DATA TIMESHARING
C 71431 - (TYPE HELP)
C 71620 - UNION CARBIDE
C 80331
C 80423 - CONTROL DATA INTERCOM
C 80424 - CONTROL DATA INTERCOM
C 80426 - BABCOCK AND WILCOX
C 81623
C 81625 - UNINET
C 81626 - UNINET
C 90995D - TELENET NEWS SERVICE
C 91930
C 91931
C 91933 C 91934
Hope you liked the post,Pass the comments............
books for hacking (self study)
Hacking: the art of exploitation
Jon Erickson - 2008 - 472 pages
Thoroughly revised and updated to incorporate the latest information on security issues, a serious introduction
to hacking describes the techniques of computer hacking, covering such topics as stack-based overflows,
format string exploits, ...
Hacking For Dummies
Kevin Beaver - 2009 - 408 pages
This guide shows you how, explains common attacks, tells you what to look for, and gives you the tools to
safeguard your sensitive business information.
Web hacking: attacks and defense
Stuart McClure, Saumil Shah, Shreeraj Shah - 2003 - 492 pages
This Web hacking volume extends the Hacking Exposed legacy into the terrain of Web vulnerabilities and
attacks.
Gray Hat Hacking
Harris - 2008
This fully updated volume offers a comprehensive overview of today's hacking and computer security
landscape.
Hacking Exposed 6
McClure - 2009
The book includes new coverage of ISO images, wireless and RFID attacks, Web 2.0 vulnerabilities, anonymous
hacking tools, Ubuntu, Windows Server 2008, mobile devices, and more.Hacking Exposed 6 applies the authors'
internationally renowned ...
An Unofficial Guide To Ethical Hacking
Ankit Fadia - 2006 - 616 pages
The basic motive behind this book is to create a new wave of ethical hackers, which would revolutionise the
global security scene.
Professional Penetration Testing: Creating and Operating a Formal ...
Thomas Wilhelm - 2009 - 504 pages
PART I - Setting Up Chapter 1: Introduction Chapter 2: Ethics and Hacking Chapter 3: Hacking as a Career
Chapter 4: Setting up Your Lab Chapter 5: Creating and Using PenTest Targets in Your Lab Chapter 6:
Hacking: digital media and technological determinism
Tim Jordan - 2008 - 160 pages
This book introduces and explains hacking in all its manifestations: crackers, open source, hacktivists and the
The social construction of what?
Ian Hacking - 1999 - 261 pages
Especially troublesome in this dispute is the status of the natural sciences, and this is where Hacking finds
some of his most telling cases, from the conflict between biological and social approaches to mental illness to
Hacking exposed VoIP
David Endler, Mark Collier, Endler - 2007
This book shows step-by-step, how online criminals perform reconnaissance, gain access, steal data, and .
Sunday, August 14, 2011
Thursday, August 11, 2011
best hacking movies ever
30. Gamer (2009)
Lionsgate Pictures
This movie is a cult favorite of video gamers: it depicts a dystopic future where the minds of state prisoners are computer-linked to the consoles of rich game players. The action is brutally violent, and the concept is over the top. But the computer graphics and special effects will slake the bloodthirst of action fans. The final 10 minutes is an eerie blend of hacking and megalomania: Michael C. Hall lipsynchs Sammy Davis Jr. while mind controlling his zombie soldiers...that scene alone is worth the price of the rental.
29. Disclosure (1994)
Warner Bros.
Disclosure is an excellent film, both for computer hacking and for the thrill of corporate espionage. A brilliant computer scientist gets passed over for a promotion, which goes to a love interest from his past. Michael Douglas and Demi Moore are splendid as this twisted plot of deceit and betrayal keeps audiences riveted for 90 minutes.
28. Swordfish (2001)
Warner Bros.
Over-the-top violence, preposterous situations, sexy women, and outstanding special effects make this a great popcorn rental. No, don't bring your brain to watch this, but if you like techno-thrillers, definitely rent this. John Travolta is the slimy villain, Hugh Jackman is the studly hero hacker, and Halle Berry is the mysterious damsel.
27. Untraceable (2008)
Sony Pictures
Untraceable is a suspenseful B-grade thriller. FBI Agent Marsh needs to stop a serial killer from slaughtering more victims, brutal acts which he broadcasts live on the Internet. Be warned: graphical violence. You'll want to watch a happy Disney movie after this disturbing cat-and-mouse thriller.
26. The Thirteenth Floor (1999)
Columbia Pictures
A very extreme version of "The Sims", this movie is about scientists who create a virtual world where participants plug in and take over a computer character's life. The characters are unaware of their puppet existence, but then a real life murder shakes the foundation of the game.
25. GoldenEye (1995)
MGM Pictures
Pierce Brosnan's 007 entry here revolves around stopping a 'Goldeneye' hacker program and weaponized satellite. Complete with beautiful female computer scientists and expensive stunt scenes, 007 takes on the digital threat using his Walther pistol and slick style.
24. Jurassic Park (1993)
Universal Pictures
This is such an entertaining movie! Even years later, the reptiles can make people jump out of their seats. And Wayne Knight portrays the loathsome hacker who steals the DNA secrets of the Jurassic project... and gets paid for his deceit in blood. Definitely rent this movie for the 5 minutes of hacker scenes, and the 110 minutes of action-adventure fun!
23. The Italian Job (2003)
Paramount Pictures
Modern heist movies always involve some sort of hacking. This particular heist movie is extremely entertaining, especially when the supposed true inventor of "Napster" is the main hacker. At least 20 minutes of hacking footage in this actioner. Definitely worth renting if you haven't seen it.
22. Tron: Legacy (2010)
Walt Disney Pictures
Most hacker movies are about heists or about virtual reality. In this latter case, Disney revisits the iconic world of "The Grid", where computer programs have become living humanoids in a gladiator-type society. While the actual hacker elements are minimal, this cult-classic sequel is a magnificently visual art film with an atmospheric sound score. Tron: Legacy is highly recommended for any fans of the original Tron, and for anyone who loves good CG effects.
21. The Net (1995)
Columbia Pictures
Sandra Bullock plays a software engineer who loses her identity to digital thieves. Filmed during the fanatic years of the then-novel World Wide Web, this film is now cliched. Nevertheless, fans of Sandra Bullock will still enjoy watching this B movie.
20. Revolution OS (2001)
Wonderview Productions
This documentary tells the story about the Linux operating system, and how it forwarded the philosophy of "open source" and free intellectual property. Not an action movie, but definitely interesting for people who want to learn more about why computer culture is the way it is. If you can find a copy of this, definitely rent it.
19. Deja Vu (2006)
Touchstone Pictures
While not exactly a 'hacking' movie, Deja Vu involves sophisticated computer intervention in time travel. Val Kilmer's team of FBI computer geeks adds technical believability to this fantastical story, the terrorism plot is harrowing, and Denzel Washington is always exciting to watch as he rushes to save the explosion victims and the pretty girls.
18. One Point O (2004)
Armada Pictures
Also known as 'Paranoia: 1.0', this film requires you to bring your brain. One Point O is a magnificent art film, and very different from Hollywood movies. An isolated young computer programmer receives mysterious packages, which leads him into a strange world of corporate conspiracy, mind control, and the bizarre lives of his neighbors. Not for impatient viewers, this film is slow, haunting, visually mesmerizing, and intensely meditative... every scene is staged to have its own special flavor. Many viewers recommend watching this film twice to catch all the clever details. If you're in that rare mood for something thought-provoking and deliberate, then definitely rent One Point O.
17. Takedown (2000)
Dimension Films
Also known as 'Track Down', this is the sensationalized story of famous phone phreaker, Kevin Mitnick. This is a definitely a B-grade movie, even a C- grade movie in many people's minds. But this flawed film is also cult classic amongst hackers.
16. Virtuosity (1995)
Paramount Pictures
Virtuosity is an interesting concept movie: the synthesizing of an artificial intelligence based on the minds of serial killers. Alas, the program manages to break free and assume physical form. It's a fantastical premise, yes, but action fans might really enjoy watching Denzel Washington chase down Russel Crowe.
15. The Core (2003)
Paramount Pictures
Disaster movies are not for everyone, but this B-movie is surprisingly entertaining. There are some noteworthy dramatic scenes and compelling themes of self-sacrifice and friendship. The "hack-the-world" segments are only about 10 minutes of the entire movie, but they are comedic segments, and should make geek-lovers smile.
14. The Lawnmower Man (1992)
Columbia TriStar
Computer imagery and hacker technology abound throughout this bizarre movie. No connection to the Stephen King story, this B-movie is an exploration of a hypothetical future where scientists can manipulate people's brains with machines and drugs. Like similar stories, the experiment breaks free, and decides to take revenge on the experimenters. While the movie production quality and acting is forgettable, the concept and themes here are strangely haunting.
13. Pirates of Silicon Valley (1999)
Warner Bros.
This is the flawed storytelling of how Apple and Microsoft came to be. While this movie got mixed reviews, many people have commented they loved it. Three dollars at your video store, and you can decide for yourself if this was a good film.
12. Antitrust (2001)
MGM Pictures
This movie has some strong points about it. Two idealistic computer whiz kids graduate from Stanford, and one of them enters the world of private sector programming. Sure enough, these two programmers find themselves in the middle of cybercrime scandals. Definitely worth renting for three bucks.
11. Hackers (1995)
United Artists
Don't bring your brain to watch this, either. The story is weak, and the hacking scenes are nowhere near reality. But you have to watch this just to say you did. You'll learn where the iconic names of "Zero Cool" and "Lord Nikon" come from. You'll hear some breakthrough techno music in the soundtrack. Plus: Angelina Jolie is reason enough for most men to rent this cult classic.
10. Foolproof (2003)
Alliance Atlantis
A lower-budget Canadian movie about hobby bank robbers, this was a delightful surprise to many viewers. Ryan Reynolds and his friends "virtually" rob banks for fun, but are blackmailed into doing a heist for real. This is a good action rental.
9. The Conversation (1974)
Paramount
While you won't see computers in this classic film, the theme of surveillance and the violation of people's privacy is so masterfully explored here.
**Related movie: The Conversation was re-imagined as Will Smith's Enemy of the State in 2001. The 2001 treatment of the story was designed as a modern techno thriller, and has some tremendous special effects and satellite surveillance sequences. Having Gene Hackman star with Will Smith makes it worth the price of a DVD rental.
8. The Matrix (1999)
Warner Bros.
This was such a groundbreaking adventure in reality and existentialism. No, you will not learn how to break into a Linux server by watching Trinity port-scanning with "nmap". But this movie is definitely cool, nonetheless.
7. The Score (2001)
Paramount Pictures
Edward Norton and Robert De Niro are fabulous in this heist flick. In a clever plot to rob a Montreal customs house of some royal artifacts, Norton and De Niro must break into the security systems with the help of a socially-awkward hacker who lives in his mother's basement. 10 minutes of hacking, and 100 minutes of phenomenal robbery storytelling!
6. Die Hard 4: Live Free or Die Hard (2007)
20th Century Fox
Leave it to Bruce Willis to save the world from uber hackers. Macintosh advertising personality, Justin Long, plays the reluctant programmer caught up in an digital terrorism scheme. Like Swordfish, this movie has over-the-top violence and outrageous action sequences, but if you liked the Die Hard series, definitely see this.
5. eXistenZ (1999)
Alliance Atlantis
A David Cronenberg film, this is the creepiest entry in the list. A game designer creates an artificial reality game that plugs directly into people's minds. The line between reality and game then blurs in a violent and gruesome way. This is very much a powerful art film, and not for everyone. Have a Disney movie ready to watch as a chaser after this show. Aptly so: our number 1 choice below is a Disney movie...
4. Wargames (1983)
MGM Pictures
Yes, this movie is very old, but it is still a pivotal film in many viewers' minds. A young man finds a back door into a military computer that is linked to the nuclear defense grid of the United States. A preposterous plot, but a compelling commentary on nuclear war and the destruction of the human race. You have to see this movie just to say you have seen it.
3. Sneakers (1992)
Universal Pictures
While dated, this movie was groundbreaking at the time, and is still charming to this day. The story revolves around two college buddies who take different paths in life. One becomes an ethical hacker, and the other...well, he is not quite so noble. Some great plot twists and comic scenes make this a good way to spend a Saturday afternoon at home.
2. The Girl with the Dragon Tattoo (2009)
Alliance Films
She's a Swedish hacker who types on a Mac and lives with Asperger's Syndrome. She teams up with a journalist to solve a murder-mystery. And she has a dragon tattoo. Based on the Stieg Larsson novels, this film has earned international acclaim, and is likely to be remade in English, perhaps with George Clooney or Brad Pitt in a lead role. Warning: this movie does have graphic sexual content.
1. Tron (1982)
Disney Pictures
A classic! A hacker is transported into the digital universe of "The Grid", and must survive combat as a cyber gladiator in order to stop the villanous Master Control. The imagination behind this movie made big ripples in the science fiction world, and today, Tron is a cult classic that every computer user should see at least once.
Lionsgate Pictures
This movie is a cult favorite of video gamers: it depicts a dystopic future where the minds of state prisoners are computer-linked to the consoles of rich game players. The action is brutally violent, and the concept is over the top. But the computer graphics and special effects will slake the bloodthirst of action fans. The final 10 minutes is an eerie blend of hacking and megalomania: Michael C. Hall lipsynchs Sammy Davis Jr. while mind controlling his zombie soldiers...that scene alone is worth the price of the rental.
29. Disclosure (1994)
Warner Bros.
Disclosure is an excellent film, both for computer hacking and for the thrill of corporate espionage. A brilliant computer scientist gets passed over for a promotion, which goes to a love interest from his past. Michael Douglas and Demi Moore are splendid as this twisted plot of deceit and betrayal keeps audiences riveted for 90 minutes.
28. Swordfish (2001)
Warner Bros.
Over-the-top violence, preposterous situations, sexy women, and outstanding special effects make this a great popcorn rental. No, don't bring your brain to watch this, but if you like techno-thrillers, definitely rent this. John Travolta is the slimy villain, Hugh Jackman is the studly hero hacker, and Halle Berry is the mysterious damsel.
27. Untraceable (2008)
Sony Pictures
Untraceable is a suspenseful B-grade thriller. FBI Agent Marsh needs to stop a serial killer from slaughtering more victims, brutal acts which he broadcasts live on the Internet. Be warned: graphical violence. You'll want to watch a happy Disney movie after this disturbing cat-and-mouse thriller.
26. The Thirteenth Floor (1999)
Columbia Pictures
A very extreme version of "The Sims", this movie is about scientists who create a virtual world where participants plug in and take over a computer character's life. The characters are unaware of their puppet existence, but then a real life murder shakes the foundation of the game.
25. GoldenEye (1995)
MGM Pictures
Pierce Brosnan's 007 entry here revolves around stopping a 'Goldeneye' hacker program and weaponized satellite. Complete with beautiful female computer scientists and expensive stunt scenes, 007 takes on the digital threat using his Walther pistol and slick style.
24. Jurassic Park (1993)
Universal Pictures
This is such an entertaining movie! Even years later, the reptiles can make people jump out of their seats. And Wayne Knight portrays the loathsome hacker who steals the DNA secrets of the Jurassic project... and gets paid for his deceit in blood. Definitely rent this movie for the 5 minutes of hacker scenes, and the 110 minutes of action-adventure fun!
23. The Italian Job (2003)
Paramount Pictures
Modern heist movies always involve some sort of hacking. This particular heist movie is extremely entertaining, especially when the supposed true inventor of "Napster" is the main hacker. At least 20 minutes of hacking footage in this actioner. Definitely worth renting if you haven't seen it.
22. Tron: Legacy (2010)
Walt Disney Pictures
Most hacker movies are about heists or about virtual reality. In this latter case, Disney revisits the iconic world of "The Grid", where computer programs have become living humanoids in a gladiator-type society. While the actual hacker elements are minimal, this cult-classic sequel is a magnificently visual art film with an atmospheric sound score. Tron: Legacy is highly recommended for any fans of the original Tron, and for anyone who loves good CG effects.
21. The Net (1995)
Columbia Pictures
Sandra Bullock plays a software engineer who loses her identity to digital thieves. Filmed during the fanatic years of the then-novel World Wide Web, this film is now cliched. Nevertheless, fans of Sandra Bullock will still enjoy watching this B movie.
20. Revolution OS (2001)
Wonderview Productions
This documentary tells the story about the Linux operating system, and how it forwarded the philosophy of "open source" and free intellectual property. Not an action movie, but definitely interesting for people who want to learn more about why computer culture is the way it is. If you can find a copy of this, definitely rent it.
19. Deja Vu (2006)
Touchstone Pictures
While not exactly a 'hacking' movie, Deja Vu involves sophisticated computer intervention in time travel. Val Kilmer's team of FBI computer geeks adds technical believability to this fantastical story, the terrorism plot is harrowing, and Denzel Washington is always exciting to watch as he rushes to save the explosion victims and the pretty girls.
18. One Point O (2004)
Armada Pictures
Also known as 'Paranoia: 1.0', this film requires you to bring your brain. One Point O is a magnificent art film, and very different from Hollywood movies. An isolated young computer programmer receives mysterious packages, which leads him into a strange world of corporate conspiracy, mind control, and the bizarre lives of his neighbors. Not for impatient viewers, this film is slow, haunting, visually mesmerizing, and intensely meditative... every scene is staged to have its own special flavor. Many viewers recommend watching this film twice to catch all the clever details. If you're in that rare mood for something thought-provoking and deliberate, then definitely rent One Point O.
17. Takedown (2000)
Dimension Films
Also known as 'Track Down', this is the sensationalized story of famous phone phreaker, Kevin Mitnick. This is a definitely a B-grade movie, even a C- grade movie in many people's minds. But this flawed film is also cult classic amongst hackers.
16. Virtuosity (1995)
Paramount Pictures
Virtuosity is an interesting concept movie: the synthesizing of an artificial intelligence based on the minds of serial killers. Alas, the program manages to break free and assume physical form. It's a fantastical premise, yes, but action fans might really enjoy watching Denzel Washington chase down Russel Crowe.
15. The Core (2003)
Paramount Pictures
Disaster movies are not for everyone, but this B-movie is surprisingly entertaining. There are some noteworthy dramatic scenes and compelling themes of self-sacrifice and friendship. The "hack-the-world" segments are only about 10 minutes of the entire movie, but they are comedic segments, and should make geek-lovers smile.
14. The Lawnmower Man (1992)
Columbia TriStar
Computer imagery and hacker technology abound throughout this bizarre movie. No connection to the Stephen King story, this B-movie is an exploration of a hypothetical future where scientists can manipulate people's brains with machines and drugs. Like similar stories, the experiment breaks free, and decides to take revenge on the experimenters. While the movie production quality and acting is forgettable, the concept and themes here are strangely haunting.
13. Pirates of Silicon Valley (1999)
Warner Bros.
This is the flawed storytelling of how Apple and Microsoft came to be. While this movie got mixed reviews, many people have commented they loved it. Three dollars at your video store, and you can decide for yourself if this was a good film.
12. Antitrust (2001)
MGM Pictures
This movie has some strong points about it. Two idealistic computer whiz kids graduate from Stanford, and one of them enters the world of private sector programming. Sure enough, these two programmers find themselves in the middle of cybercrime scandals. Definitely worth renting for three bucks.
11. Hackers (1995)
United Artists
Don't bring your brain to watch this, either. The story is weak, and the hacking scenes are nowhere near reality. But you have to watch this just to say you did. You'll learn where the iconic names of "Zero Cool" and "Lord Nikon" come from. You'll hear some breakthrough techno music in the soundtrack. Plus: Angelina Jolie is reason enough for most men to rent this cult classic.
10. Foolproof (2003)
Alliance Atlantis
A lower-budget Canadian movie about hobby bank robbers, this was a delightful surprise to many viewers. Ryan Reynolds and his friends "virtually" rob banks for fun, but are blackmailed into doing a heist for real. This is a good action rental.
9. The Conversation (1974)
Paramount
While you won't see computers in this classic film, the theme of surveillance and the violation of people's privacy is so masterfully explored here.
**Related movie: The Conversation was re-imagined as Will Smith's Enemy of the State in 2001. The 2001 treatment of the story was designed as a modern techno thriller, and has some tremendous special effects and satellite surveillance sequences. Having Gene Hackman star with Will Smith makes it worth the price of a DVD rental.
8. The Matrix (1999)
Warner Bros.
This was such a groundbreaking adventure in reality and existentialism. No, you will not learn how to break into a Linux server by watching Trinity port-scanning with "nmap". But this movie is definitely cool, nonetheless.
7. The Score (2001)
Paramount Pictures
Edward Norton and Robert De Niro are fabulous in this heist flick. In a clever plot to rob a Montreal customs house of some royal artifacts, Norton and De Niro must break into the security systems with the help of a socially-awkward hacker who lives in his mother's basement. 10 minutes of hacking, and 100 minutes of phenomenal robbery storytelling!
6. Die Hard 4: Live Free or Die Hard (2007)
20th Century Fox
Leave it to Bruce Willis to save the world from uber hackers. Macintosh advertising personality, Justin Long, plays the reluctant programmer caught up in an digital terrorism scheme. Like Swordfish, this movie has over-the-top violence and outrageous action sequences, but if you liked the Die Hard series, definitely see this.
5. eXistenZ (1999)
Alliance Atlantis
A David Cronenberg film, this is the creepiest entry in the list. A game designer creates an artificial reality game that plugs directly into people's minds. The line between reality and game then blurs in a violent and gruesome way. This is very much a powerful art film, and not for everyone. Have a Disney movie ready to watch as a chaser after this show. Aptly so: our number 1 choice below is a Disney movie...
4. Wargames (1983)
MGM Pictures
Yes, this movie is very old, but it is still a pivotal film in many viewers' minds. A young man finds a back door into a military computer that is linked to the nuclear defense grid of the United States. A preposterous plot, but a compelling commentary on nuclear war and the destruction of the human race. You have to see this movie just to say you have seen it.
3. Sneakers (1992)
Universal Pictures
While dated, this movie was groundbreaking at the time, and is still charming to this day. The story revolves around two college buddies who take different paths in life. One becomes an ethical hacker, and the other...well, he is not quite so noble. Some great plot twists and comic scenes make this a good way to spend a Saturday afternoon at home.
2. The Girl with the Dragon Tattoo (2009)
Alliance Films
She's a Swedish hacker who types on a Mac and lives with Asperger's Syndrome. She teams up with a journalist to solve a murder-mystery. And she has a dragon tattoo. Based on the Stieg Larsson novels, this film has earned international acclaim, and is likely to be remade in English, perhaps with George Clooney or Brad Pitt in a lead role. Warning: this movie does have graphic sexual content.
1. Tron (1982)
Disney Pictures
A classic! A hacker is transported into the digital universe of "The Grid", and must survive combat as a cyber gladiator in order to stop the villanous Master Control. The imagination behind this movie made big ripples in the science fiction world, and today, Tron is a cult classic that every computer user should see at least once.
Friday, July 22, 2011
Tuesday, July 5, 2011
windows user account Attacks
step1:
open command prompt.
step2:
use the command in the command prompt
"Net User username *"
note:
1):type a new password to reset the hash.
2):leave blank and hit enter to remove the password.
3):here user name is account name.
so enjoy with other lapi.
open command prompt.
step2:
use the command in the command prompt
"Net User username *"
note:
1):type a new password to reset the hash.
2):leave blank and hit enter to remove the password.
3):here user name is account name.
so enjoy with other lapi.
just do it !!!!
step1:
go to command prompt
step2:
write "msconfig" to minimize boot time and services.
or
write "ipconfig" to know ip of system
or
write "ping 'website_name'" to know ip of that particular site.
or
write "systeminfo" to know detail of the system configuration.
or
write "getmac" to know the mac add. of the system.
or
write "iexpress" to make hidden any soft behind any software.
so just enjoy these facility ...............
go to command prompt
step2:
write "msconfig" to minimize boot time and services.
or
write "ipconfig" to know ip of system
or
write "ping 'website_name'" to know ip of that particular site.
or
write "systeminfo" to know detail of the system configuration.
or
write "getmac" to know the mac add. of the system.
or
write "iexpress" to make hidden any soft behind any software.
so just enjoy these facility ...............
Tuesday, June 14, 2011
hide a massage behind any image or file(stenography)
step1:
open notepad and write down secret msg.
step2:
save it.
step3:
open command prompt and write down
copy /b image_name.jpg+secret.txt new_image.jpg
example: copy \b malika.jpg+sajani.jpg sajanifinal.jpg
step4:
enjoy your communication
note:
1.file format should be same of source image and final image .
2.open file with notepad and msg will be end of file you can search string.
open notepad and write down secret msg.
step2:
save it.
step3:
open command prompt and write down
copy /b image_name.jpg+secret.txt new_image.jpg
example: copy \b malika.jpg+sajani.jpg sajanifinal.jpg
step4:
enjoy your communication
note:
1.file format should be same of source image and final image .
2.open file with notepad and msg will be end of file you can search string.
how to make virus (bat file)
step1:
open notepad
step2:write this code
:hack
start notepad.exe
start explorer.exe
start calc.exe
goto hack
step3:
save this file with name hack.bat
step4:
just click on the file & magic will began
note:-
1.file should be save with .bat extension
2.u can include many more programs in code
3.u can get code from C:\Windows\System32
or start task manager goto process explorer and get program name.
so enjoy ..............
open notepad
step2:write this code
:hack
start notepad.exe
start explorer.exe
start calc.exe
goto hack
step3:
save this file with name hack.bat
step4:
just click on the file & magic will began
note:-
1.file should be save with .bat extension
2.u can include many more programs in code
3.u can get code from C:\Windows\System32
or start task manager goto process explorer and get program name.
so enjoy ..............
Sunday, April 10, 2011
Wednesday, April 6, 2011
Sunday, April 3, 2011
Thursday, March 31, 2011
Subscribe to:
Posts (Atom)